pfsense installation with IPSec VPN and iOS client setup (updated)
(Last updated at 2010.05.08)
After tryout ClearOS 5.2, I encountered some problem which is too difficult to overcome. For example, the routing speed is very slow (I am running under VMware ESX 5 with a Broadcom NIC), the firewall setting of ClearOS is too simple, I cannot manage to make PPTP client to connect with devices on LAN, etc.
Finally I decided that I need to switch to another Firewall. I pick pfsense 2.0.1.
64 bit vs 32 bit
At first I tried to install the 64 bit version, but I read some forums, there are some issues that only occurs on 64 bit version. Their official page also mentioned that 32 bit version is more mature. To save my time on identifing whether is my setting error or a software bug, I decided to switch back to 32 bit installation.
IPSec VPN with iPhone
I found this document at official site very useful for setup iPhone with VPN.
The original document lacks some screen dump. Beginner of pfsense may find it difficult to follow. Base on the original document, I have added screen dumps and some of my comments/correction below:
After tryout ClearOS 5.2, I encountered some problem which is too difficult to overcome. For example, the routing speed is very slow (I am running under VMware ESX 5 with a Broadcom NIC), the firewall setting of ClearOS is too simple, I cannot manage to make PPTP client to connect with devices on LAN, etc.
Finally I decided that I need to switch to another Firewall. I pick pfsense 2.0.1.
64 bit vs 32 bit
At first I tried to install the 64 bit version, but I read some forums, there are some issues that only occurs on 64 bit version. Their official page also mentioned that 32 bit version is more mature. To save my time on identifing whether is my setting error or a software bug, I decided to switch back to 32 bit installation.
IPSec VPN with iPhone
I found this document at official site very useful for setup iPhone with VPN.
The original document lacks some screen dump. Beginner of pfsense may find it difficult to follow. Base on the original document, I have added screen dumps and some of my comments/correction below:
IPsec Server Setup
This is the setup for the pfSense side of the connection
Mobile Clients
- Check "Enable IPsec Mobile Client Support"
- Check "Provide a virtual IP address to clients" (I use 192.168.3.0 in this example)
- Enter an unused subnet in the box, pick a subnet mask (I use 24 bit net mask in this example)
- Set any other desired options here
- (my comment: If you want your iPhone to be able to connect to Internet after IPSec connected, you need to push your own DNS server (usually your router address), or Google's DNS address to your iPhone, so to resolve server name correctly.)
- Save, apply, create p1 if it doesn't exist.
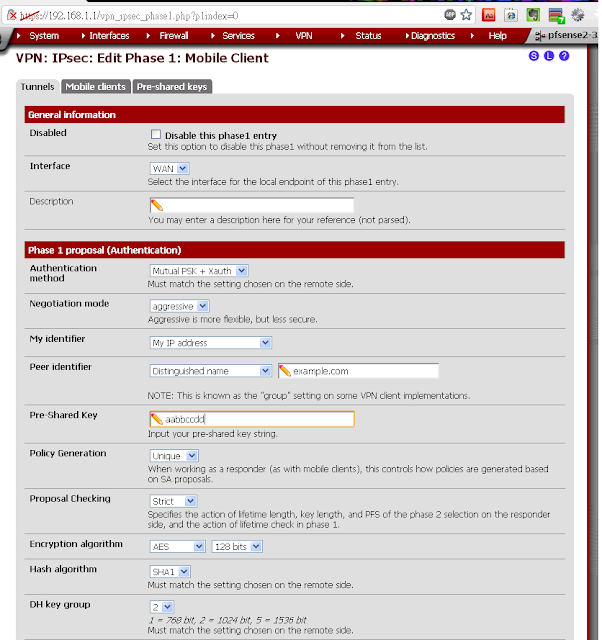
Phase 1 settings
- Authentication method: Mutual PSK + Xauth
- Negotiation mode: aggressive
- My identifier: My IP address
- Peer identfier: User Distinguished Name,
vpnusers@example.comexample.com - Pre-Shared Key: aaabbbccc
- Proposal Checking: Obey
- Encryption Algorithm: AES 128
- Hash Algorithm: SHA1
- DH Key Group: 2
- Lifetime: 86400
- Save
- NOTE: Some have had more success with the following settings:
- Policy Generation: Unique
- Proposal Checking: Strict
- NAT Traversal: Force
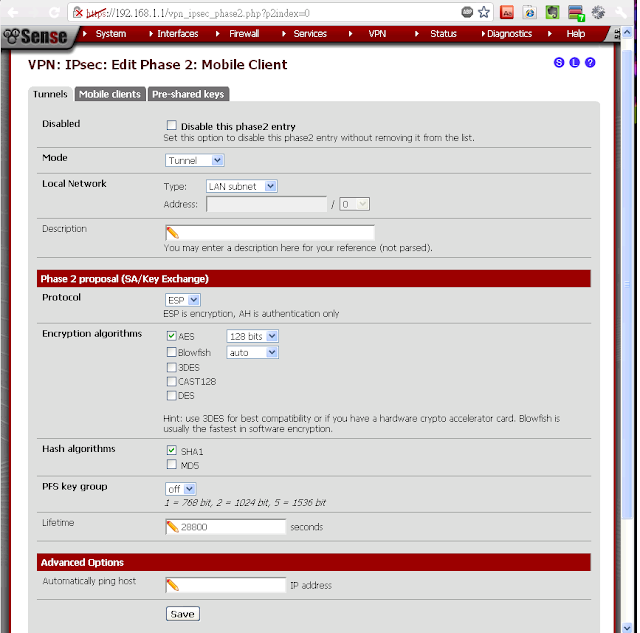
Phase 2 settings
- Mode: Tunnel
- Local Network: (your local network)
- Protocol: ESP
- Encryption Algorithms: AES 128 *only*
- Hash Algorithms: SHA1 *only*
- PFS key group: off
- Lifetime: 28800
- Save, apply
User Settings
- Go to System > User Manager
- Add a user,
- Assign a user password (this password will be required during login at iPhone
- Under "Effective Privileges", grant the user the "User - VPN - IPSec xauth Dialin" permission, or add to a group with this permission
- For "IPsec Pre-Shared Key" field: This is used for non-xauth IPsec. Please leave it as blank because we have chosen Xauth in previous steps.
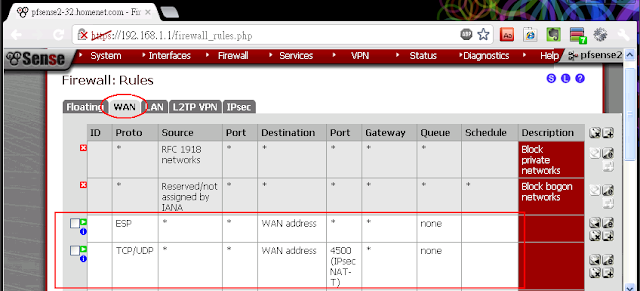
Firewall Rules
Don't forget to add firewall rules to accept client connection from WAN interface:
- Firewall > Rules, WAN tab
- Add one rule for the ESP traffic
- Add another rule for the IPSec NAT-T traffic
- The result rules for WAN interface will be like this
Don't forget to add firewall rules to pass traffic from clients
- Firewall > Rules, IPsec tab
- You may add rules that match the traffic you want to allow, or add a rule to pass any protocol/any source/any destination to allow everything. In this example, I simply add one rule to allow IPSec client to connect to both internal hosts as well as Internet.
- The result will be like this
For NAT, no special NAT rule is needed. The system will perform automatic NAT on outbound traffic.
Device Setup (iOS)
- Settings > General > Network > VPN
- Add VPN Configuration
- Click IPsec
- Description: whatever you want
- Server: IP of the server (or you may use Dynamic DNS if you don't have a fix IP)
- Account: your xauth username
- Password: your xauth password (or leave blank to be prompted every time)
- Group Name:
vpnusers@example.comexample.com - Secret: PSK from the Phase 1 above (in my example, it should be aabbccdd)







Comments